GDPR and IT Operations Pt. 3 – Resources
This is a blog series of three on the topic of GDPR, and more specifically some of the practical challenges it can pose to IT Operations when it comes to auditing and documenting access control.
Part 1: What users in your network has access to information.
Part 2: How does those users access data (user groups)
In this post we will be moving on from the Whos and the Hows to the Whats (Resources/Data). In other words, the resources your users are accessing are in focus. Like with the former two posts, this is reading that can interest non vScope users as well, since it gives some general hints and tips on auditing. Hope you will enjoy!

Customer Success
GDPR for IT – IT Documentation and Access Control
To this day, our industry still has plenty of manual routines, and with it comes errors and mistakes. This post can help you with some of the auditing needed to be done from an IT Operations perspective in order to meet GDPR compliance by May. But most importantly; it will show you how to build dynamically updating IT documentation to keep at hand onward!
The critical part of GDPR is not really about meeting compliance in time. For IT Operations, focus will have to be on constantly maintaining a high level of control over things like access rights and storage of certain types of data. The main concern is minimizing the risk for errors and mistakes, and identifying them quickly should they come along. Now for THIS, vScope is an (almost) fix it for you kind of product! Let’s have a look at some of the things we can do for you!
Requirements for this tutorial
- The environment in focus for this analysis is a Microsoft environment set up with standard solutions for access control
- In order to follow this tutorial you will need:
- vScope Server subscription
- vScope Directory subscription
- vScope Database subscription
- or to be running a trial license
- The screenshots in this tutorial are from a vScope with all products licensed
Pt. 3 – Resources
Often, when we hear the term “personal data” in relations to GDPR, it is in the context of business intelligence and big data. Of course, specific issues such as the legitimacy of “soft opt-ins” has less impact on you if you work in IT Operations. It might make you feel that GDPR is more of a headache for the marketing department than it is for you. However, the focus placed on marketing issues tends put questions about other types of personal data in the shadow. There is still plenty you need to stay on top of!
Many types of personal data are handled by IT Operations. An obvious example would be the databases for your organizations HR-system. But there is more:
- Mailboxes are a standard example, quite likely containing a mixture of organizational information and some personal emails.
- The user profile of an employee, likely stored in parts both locally on machines and on a server file share in case you use roaming profiles. User profiles can contain things like a personal download folder, browsing history, pictures, saved passwords etc. All sensitive personal data.
- Do your managers store documentation of personal meetings with employees on shares? Most likely, and that documentation is in parts sensitive personal data too.
Even though there is a high likeliness that all of the data listed above lawfully belongs to your organization, it is personal and you cannot do as you please with it. You need to have a strategy for handling it.
Identifying personal data
You can’t go out on a mission to find every last bit of personal data stored within your organization. That is a lost cause. What you can do, is document the most common stores for it. No updated IT documentation at hand to use as a basis for your work? Well, now is the time to build it!
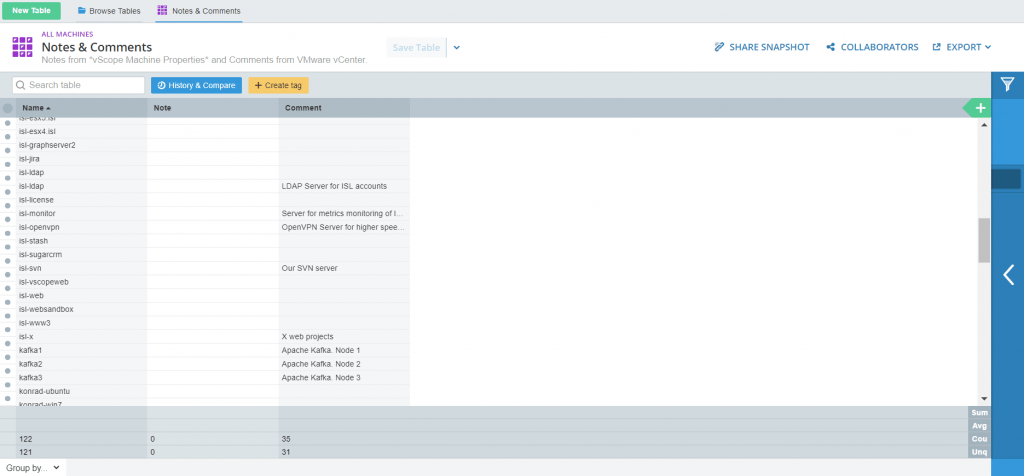
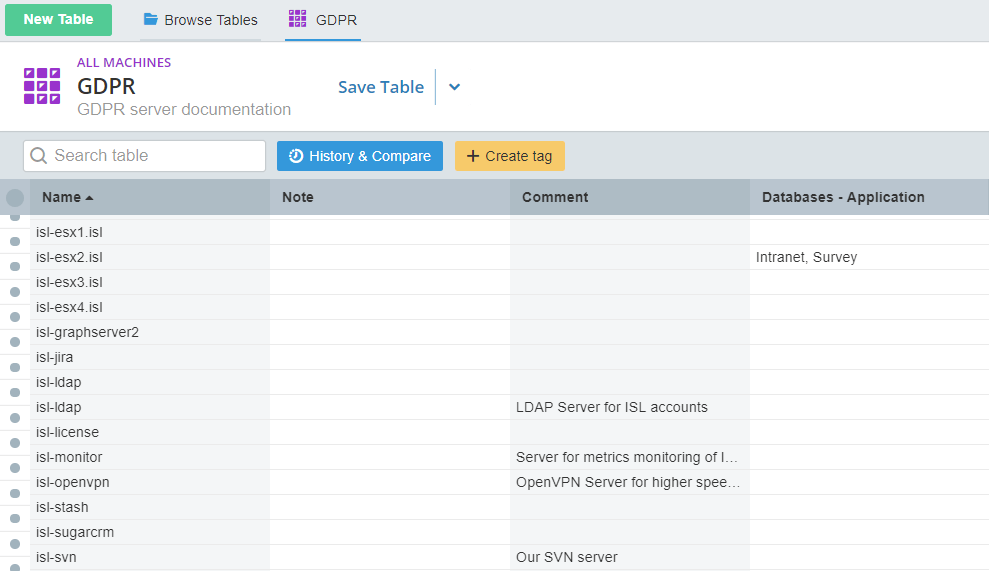
Start out with checking your environment for notes and comments. vScope has a table presenting those sections from VMware.
Consulting some key people in the organization is a good idea. Your colleagues within IT, of course. IT-architects, database administrators, application specialists, those should all be asked to give a list of systems possibly containing sensitive personal data. Are all those roles filled by you? Well, make sure to consult your colleagues anyway, Even a renaissance person needs a helping hand every now and then. 🙂
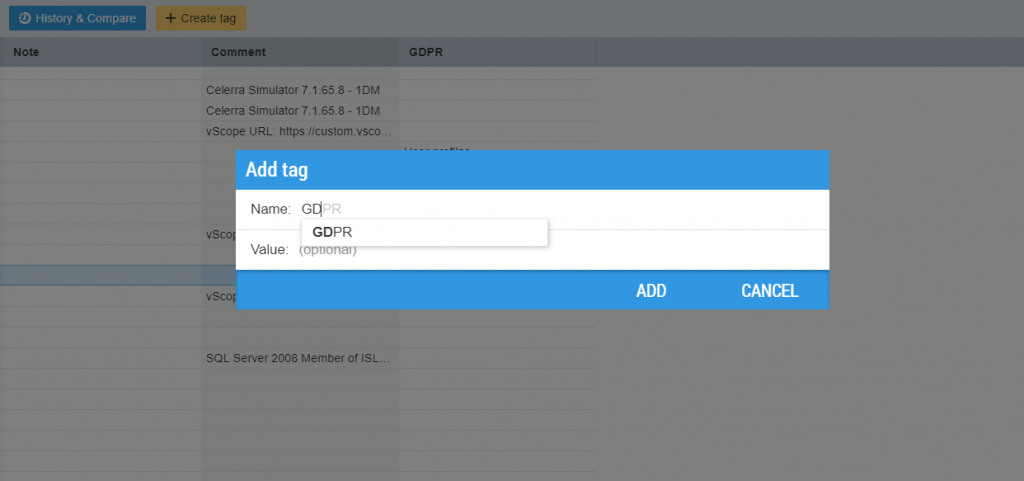
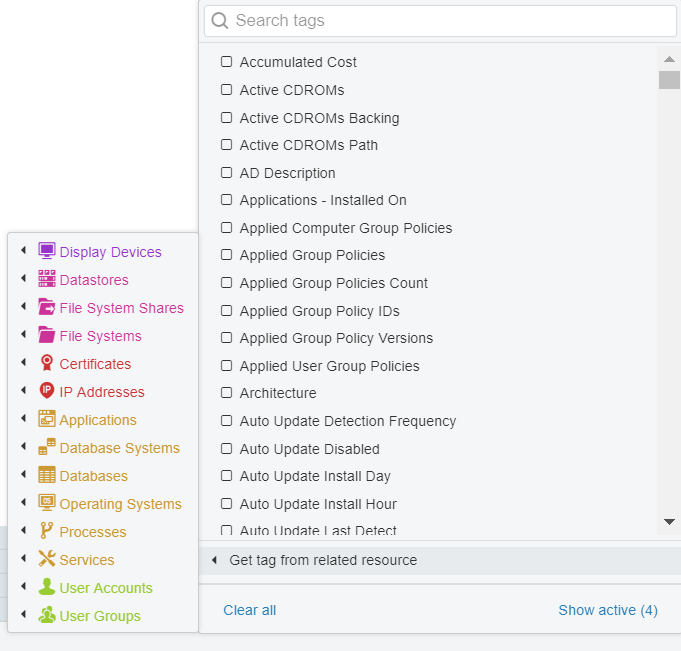
Move on, outside of IT. Start with HR. Make sure you document any system you find. Try using a manual tag in vScope for it! Why not create a GDPR tag? Use it, not just to specify that a system holds personal data, but also of what type. Simply right click an object from Table Explorer and choose “Add tag”. As soon as a tag is created, it can be opened as a column. Tags are case sensitive. As long as you name them identically, they will sort themselves into the same column. Start typing the tag, and it will be suggested, like so:
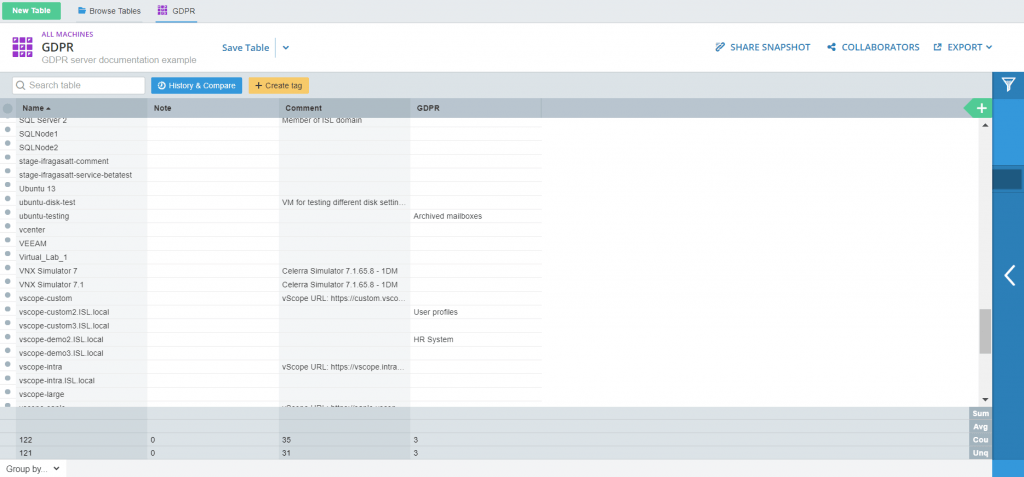
By now, with the GDPR tagging our list might look something like this:
Tip#1 You can create both manual and dynamic tags for any type of resource you have allowed vScope to scan. Learn more about working with tags here.
Types of data
vScope can help you identify plenty of different types of data stores. These following screenshots will show you some common examples of data that in one way or another gets handled directly by IT Operations, illustrated with the tables you can build for them.
Databases
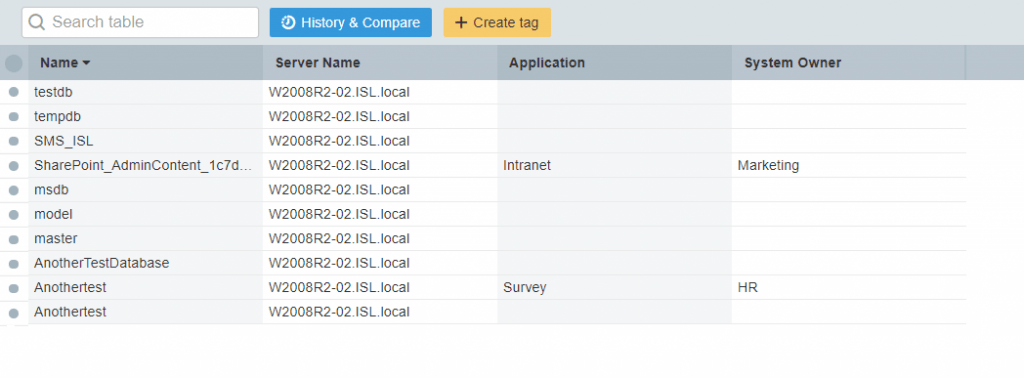
Within your general organization, personal data can often be found in the databases connected to HR systems, different kinds of survey systems and documentation systems for managers. Get a quick overview of all your databases by opening up New Table -> Databases. Take the time to tag your databases with any important information you come across, such as the application it is connected to, or the department/user that is currently the system owner.
Tip#2 Are you a database admin, or involved in a database migration project? Then this post about rightsizing is for you!
Try switching back to a server list. This time, try “Get tag from a related resource” and choose Databases -> Applications.
Now those tags you placed on your databases can be used to give you a view of what servers are connected to applications handling sensitive data!
File shares
File shares are used to hold documents (among other things). This is the sort of place where you might find protocols from meetings, or where managers can choose to store quite sensitive information such as notes from one on ones with employees. As users, we only see the part of a folder structure that we ourselves are allowed access to. But from an admin perspective we realize how incredibly complicated folder sharing permissions are, and how easily things can go wrong through dragged and copied folders and inheritance issues.
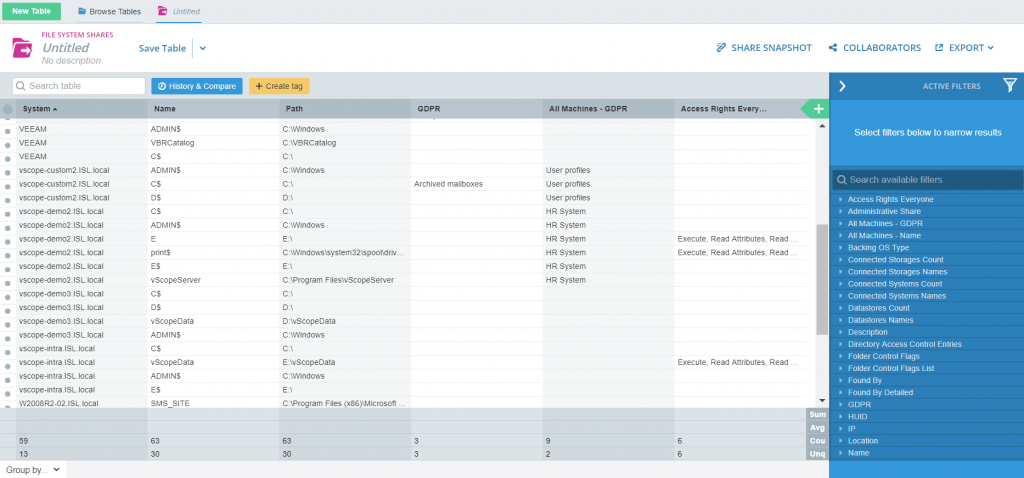
Open up File System Shares in Table Explorer. You will want to use tagging according to the same principles here that we have gone through previously. Mark up the purpose of shares, and perhaps a manager/owner of a share. You might possibly want to be working with some kind of sensitivity level for data. That can be tagged to.
Check permissions for the more sensitive shares. Are any of them set to for example give “Everyone” read or even write-permissions? That might be an issue, in that case worth following up on.
Tip#3 Try this KB for a quick guide into viewing folder permissions and sorting out your group nesting.
Tagging with geographic location
GDPR statutes some restrictions on cross border data transfer. Simply put: If your infrastructure is spread out across an international environment, you might not be able to freely move personal data around across your servers. You need to consult the person your organization has named as GDPR responsible, in order to sort out what your policy is. Then, if it turns out that you do need to keep an eye on the geographic location of some data, and track it if it is moved, vScope can help! Here are some things you can do:
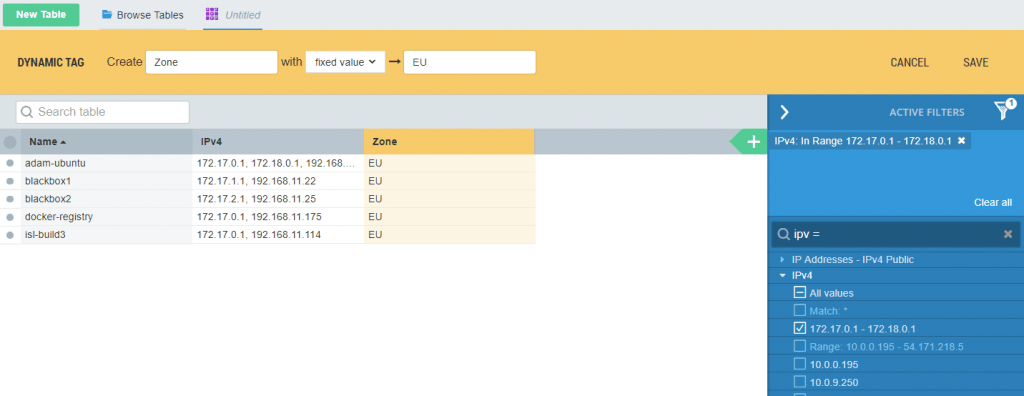
Use a dynamic tag, set to IP-ranges, to document the geographic belongings of data. Start with clicking “Create tag” above a table in Table Explorer. Name it something like “Zone” and dedicate ranges to zones like “EU” and any applicable areas outside of the EU.
You can play around with different options here, like for example building a tracker that notifies you when the Zone has changed for a server that holds shares tagged Sensitive.
Remember: Some possible breaches to GDPR needs to be investigated and possibly reported within 70 hours. Because of this, it can be a good idea to share the tables and trackers you have built with GDPR responsible parties within your organization. Making them vScope Viewers will let you do that!
Recap: Results of GDPR Resources/Data analysis
In conclusion: personal data is stored everywhere within your server environment, and access control is needed everywhere. Even with automation of things like administrating user accounts, you will always need to do regular auditing of your systems.
This series has gone through different ways of auditing and documenting User Accounts, Groups and now lastly Data. Setting up tables and trackers along the lines of the examples shown, or according to other preferences, will help you in both keeping documentation ready at hand and enable you to react fast upon unauthorized changes. These are requirements to be GDPR compliant.
Just don’t leave it all up to vScope. People are key! 😉
Read more
Sign up for newsletter
Join our community and 1000+ IT professionals by signing up for blogs, news and business insight through our newsletter